! Name the NAT for the servers pptp responses
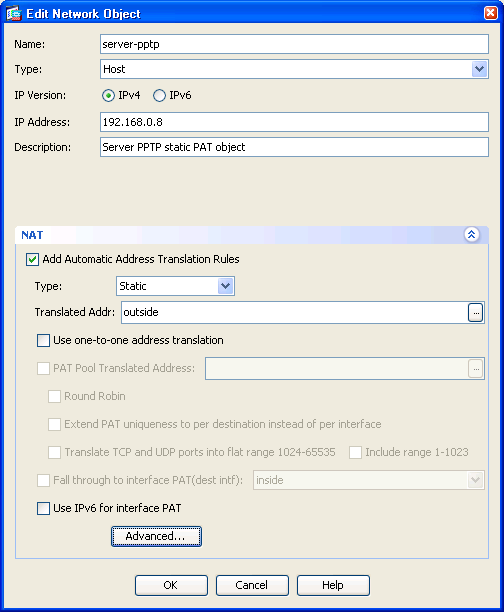 object network server-pptp
object network server-pptphost server
! replace server with actual IP of server... can't use object-network names here
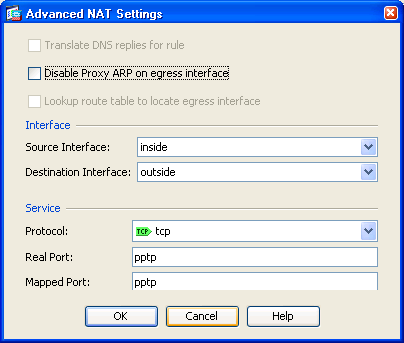 nat (inside,outside) static interface service tcp
1723 1723
nat (inside,outside) static interface service tcp
1723 1723
Notes:
After connecting to the console, you will see the router> prompt where "router" is replaced with the name of the device. Use the enable command to enter EXEC mode. The password is empty by default (just press enter). The prompt should change to router#
To go into configuration mode, at the router# prompt, type conf
t:
router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
router(config)#
The router responds with a new prompt showing the mode. To exit, enter Ctrl+Z
To see the types of access lists which are possible, at the router config
prompt:
router(config)#access-list ?
To see the current access lists:
do show access-list
the "do" is required in config mode. Outside config mode, just start with
show.... The result will show each line of each access list with a sequence
number before each line.
Router#do show access-list
Extended IP access list 101
10 permit tcp any any
20 permit udp any any
30 permit icmp any any
To add a new entry in an access list, specify which ACL you are adding then
entry into, then permit or deny, then the source and wildcard
access-list [1-99] [permit|deny] [source wildcard|host
source|any]
wildcard bits are the invoice of the subnet mask. Subtract subnet from
255.255.255.255 to find the wildcard. host is used to specify an
individual computer, so that the 0.0.0.0 wildcard is not required. E.g.
192.168.0.8 0.0.0.0 can be replaced with host 192.168.0.8.
any refers to any address on the network.
e.g. to permit traffic from the entire 192.168.0 class C local network.
All other traffic will be denied (by default).
router(config)#access-list 2 permit 192.168.0.0 0.0.0.255
Remember, access lists do /nothing/ until applied to an interface. For a
list of interfaces,
router(config)#do show ip int brief
Again, the do is required in config mode. Despite an interface being listed
as e.g. "GigabitEthernet0/0", you can reference that as g0/0.
To add an access list to an interface:
router(config)#int g0/0
router(config-if)#ip access-group 2 out
where g0/0 is the interface (in this example, it should be connected to our
LAN), and we applied access list 10 (a standard ACL) and we applied to to
traffic going in to the router from the lan. It is better to apply ACL's
to the port closest to the source of the traffic, unless the traffic could
be coming from many different interfaces, because then the router only has
to process the packets once... on the way in.
However, standard ACL's only block by source, so if you need to allow some sources to reach the destinations on one interface, but not reach destinations on another interface, you must apply them at the destination; at the interface where those sources must be blocked... or, of course, you must use extended ACL's (below). If we wish to restrict traffic as it enters the router, blocking all sources denyed in the ACL from reaching all destinations on this router, we would use in instead of out at the end of the line and attach the ACL to the interface nearest those sources.
Note the syntax here is "access-group" and NOT "access-list" even though you are referring to an ACL.
When finished configuring an interface, use:
exit
to leave (config-if) and return to the (config) prompt
To remove an access list, use the "no" command:
router(config)#no access-list 2
where 2 is the number of the ACL.
We can add comments to each ACL with the remark command
router(config)#access-list 2 remark whatever we want to
type
everything after "remark" becomes the remark and will be displayed in the
list of ACLs.
access-list [100-199] [permit|deny] [protocol] [source wildcard|host source|any] [dest wildcard|host dest|any] [eq port|gt port|lt port|neq port|range port port|any] [time-range time-range-name]
Examples:
access-list 100 deny tcp any 192.168.0.0 0.0.0.255 eq telnet
can't telnet into the local 192.168.0.0 class C network
access-list 100 deny icmp any host 192.168.0.8 echo
the machine at 192.168.0.8 won't respond to pings
access-list 100 permit tcp any host 192.168.0.8 eq 80
192.168.0.8 is a web server
access-list 100 permit ip any 192.168.0.0 0.0.0.255 any
the local C network is wide open.
router(config)#time-range WORK
router(config-time-range)#periodic Monday Tuesday Wednesday Thursday
08:00 to 17:00
router(config-time-range)#access-list 100 permit ip any any time-range
WORK
We can insert entries between existing sequence numbers (which are automatically assigned by the router) by entering the list, then specifying new sequence numbers.
Router(config)#ip access-list extended 101
Router(config-ext-nacl)#5 deny tcp any any eq telnet
We can also remove an entry by re-typing it exactly preceeded with the "no"
command: Router(config-ext-nacl)#no permit icmp any any
Router(config-ext-nacl)#exit
Router(config)#exit
Router#
However, it is very easy to make a mistake and loose the entire ACL. Instead,
copy the configuration of the router to a TFTP server or a text editor such
as Notepad in order to edit numbered ACLs. Then make any changes, disable/delete
the ACL,
Router(config)#no access-group ip 101
(note "access-group" instead of "access-list") and copy the configuration
back to the router.
E.g.
router(config)#object-group network USERS
router(config-network-group)#192.168.0.32 255.255.255.240
router(config-network-group)#192.168.0.65 255.255.255.240
router(config-network-group)#access-list 100 permit ip object-group USERS
any
As of IOS version 11.2 (12.0?), IOS XE v2.1, IOS XR 3.5, NX-OS 4.0 Access Lists can be named and each NACL can have multiple entries under one name. Both standard and extended versions are supported, but standard would typically only be used to reduce load on a heavily used system.
router(config)#ip access-list extended name
!and now the syntax is the same as the extended access list, but we can have
multiple lines. e.g.
router(config-ext-nacl)#deny icmp host 192.168.1.2 172.16.0.0
0.0.255.255
router(config-ext-nacl)#permit icmp any any
router(config-ext-nacl)#exit
for more, see:
The following applies to ASA version 9.1 only. For older commands, see older guides.
object network server-www
host server
! replace server with actual IP of server... can't use object-network
names here
nat (inside,outside) static interface service tcp 80 80
access-list outside_access_in extended permit tcp any object server-www
eq 80
! this assumes you want any to be able to access the web server.
access-group outside_access_in in interface outside
Note: You do not need to reference the network object (e.g. server-www) in the access-list; you can reference just host A.B.C.D. of the server or a generic network-object for the server directly if you like. In fact, you can just have one ACL entry for all the services by using a service object group: You still DO need to do the object network, host, nat stuff for each service, but this rolls all the ACL stuff into one command.
object-group service server-services tcp
port-object eq www
port-object eq https
port-object eq smtp
group-object smtps
object network server
host server
! replace server with actual IP of server...
access-list outside_access_in extended permit tcp any object server
object-group server-services
! this assumes you want any to be able to access these server services.
access-group outside_access_in in interface outside
object network server-rdp
host server
! replace server with actual IP of server... can't use object-network
names here
nat (inside , outside) static interface service tcp 3389 3389
! build up a list of users
object network user1
host 108.47.9.230
object network user2
host 108.47.8.122
! Put the users in a group so you can easily change who gets in.
object-group network rdppusers
network-object object user1
network-object object user2
access-list outside_access_in extended permit tcp object-group rpdpusers
object server-rdp eq 3389
access-group outside_access_in in interface outside
Is that supposed to be server-rdp or just the server? E.g. should we be
referencing the network object with the nat, or just the server ip? Or does
it not matter?
ANSWER: It doesn't matter... In fact, you can just have one ACL entry for
all the services
Note: The old PIX system provided PPTP service. ASA's do NOT provide PPTP, but can be setup to support access to an internal PPTP server from the outside.
PPTP uses both the PPTP port 1723 and the GRE service, however multiple pro's
say there is no need to permit GRE, but that may be because generally all
internal traffic is allowed out. So a minimal setup is:
access-list 100 permit tcp host 108.47.9.230 host
192.168.0.8 eq 1723
They do, however say you need to NAT responses
^
^ so a more complete
config, using object names is:
! Name the NAT for the servers pptp responses
 object network server-pptp
object network server-pptp
host server
! replace server with actual IP of server... can't use object-network
names here
 nat (inside,outside) static interface service tcp
1723 1723
nat (inside,outside) static interface service tcp
1723 1723
! build up a list of users
object network user1
host 108.47.9.230
object network user2
host 108.47.8.122
! Put the users in a group so you can easily change who gets in.
object-group network pptpusers
network-object object user1
network-object object user2
! ACL for pptp users to get to the server from outside.
access-list outside_access_in extended permit gre object-group pptpusers
object server
access-list outside_access_in extended permit tcp object-group pptpusers
object server-pptp eq pptp
access-group outside_access_in in interface outside
Is that supposed to be server-pptp or server? E.g. should we be referencing the network object with the nat, or just the regular one? Or does it not matter?
Assuming you already have net setup to allow traffic from inside to go out, just add pptp inspection.
! Inspect pptp traffic.
policy-map global_policy
class inspection_default
inspect pptp
Note: Should you choose to enable a VPN, using the Cisco or the SBS built-in VPN, the site from which a client connects, must use a different Network ID (Subnet) than that of the SBS LAN. As a result, nobody connecting from a remote site that uses 192.168.1.x locally can connect to resources on this network. Therefore it is always a best practice to avoid common subnets like; 192.168.0.x, 192.168.1.x, 192.168.2.x, 192.168.100.x 10.0.0.x, and 10.10.10.x.
See also:
| file: /Techref/inet/ciscoacls.htm, 16KB, , updated: 2016/2/11 15:34, local time: 2025/6/7 04:55,
216.73.216.36,10-1-134-241:LOG IN
|
| ©2025 These pages are served without commercial sponsorship. (No popup ads, etc...).Bandwidth abuse increases hosting cost forcing sponsorship or shutdown. This server aggressively defends against automated copying for any reason including offline viewing, duplication, etc... Please respect this requirement and DO NOT RIP THIS SITE. Questions? <A HREF="http://sxlist.com/Techref/inet/ciscoacls.htm"> Cisco Access Control Lists</A> |
| Did you find what you needed? |
Welcome to sxlist.com!sales, advertizing, & kind contributors just like you! Please don't rip/copy (here's why Copies of the site on CD are available at minimal cost. |
|
Ashley Roll has put together a really nice little unit here. Leave off the MAX232 and keep these handy for the few times you need true RS232! |
.